How does Bosch Configuration Manager handle controlled folder access and data security?
Question
How does Bosch Configuration Manager handle controlled folder access and data security?
Answer
Bosch Config Manager’s way of using controlled folder:
1. Technical context
"Controlled folder access works by only allowing trusted apps to access protected folders. Protected folders are specified when controlled folder access is configured. Typically, commonly used folders, such as those used for documents, pictures, downloads, and so on, are included in the list of controlled folders.
Controlled folder access works with a list of trusted apps. Apps that are included in the list of trusted software work as expected. Apps that are not included in the list are prevented from making any changes to files inside protected folders.
Apps are added to the list based upon their prevalence and reputation. Apps that are highly prevalent throughout your organization and that have never displayed any behavior deemed malicious are considered trustworthy. Those apps are added to the list automatically.
Apps can also be added manually to the trusted list by using Configuration Manager or Intune. Additional actions can be performed from the Microsoft Defender portal."
2. Summary
Bosch Configuration Manager (CM) application offers the user various options to define the best suitable storage location for CM’s application data. The CM does not mandate to use only controlled folders like documents or pictures. During CM’s installation the user can influence the target folder for program files and application data files. Depending on user’s choice the installation program creates required subfolders below the folder, which is defined by Windows system variables %ProgramFiles% or %LOCALAPPDATA%. CM will exclusively use the created subfolders and respective child folders during operation (“Bosch\VIDOS”); it will never use the parent directories like c:\Users\<username>\Documents.
The application data, which is stored in afore mentioned folders is inherently important for the successful operation of the CM application. Application data consists of configuration data of the user’s device network he needs to manage or license files for enabling certain features in his devices or log files just to name some examples. A detailed list can be found in the next chapter.
CM installation files are checked against anti-virus scanners before they get packed into an executable installation file and signed by Bosch. This file is scanned again before uploaded to Bosch Download Area.
Note
Bosch Configuration Manager is not the same application as MS Configuration Manager mentioned in the previous chapter.
3. Folders used
Depending on the option selected the setup application will create required installation locations during installation.
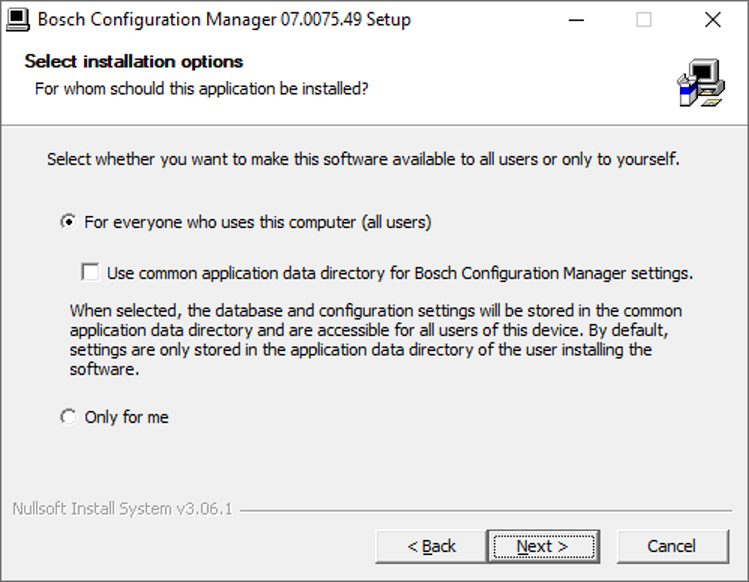
In case of selecting “For everyone who uses this computer (all users)”
Default installation location is “%ProgramFiles%\Bosch\ConfigManager” – can be changed by user during installation
In case of selecting “Only for me”
Default installation location is “%LOCALAPPDATA%\Bosch\ConfigManager” – can be changed by user during installation
Depending on installation option “Use common application data directory for Bosch Configuration Manager” setting application data root folder is set to one of following:
%APPDATA%\Bosch\VIDOS – when option is not selected
%ProgramData%\Bosch\VIDOS – when option is selected
In the current document the path will be named %CM_APPDATA% to ensure unambiguity.
3.1. Information stored in %CM_APPDATA%
CA – private Micro CA data, cash of certificates
certificates – certificate cache, needed for micro ca
conf – application configuration files
vca/CT – Camera trainer samples
The selection of “Use common application data directory for Bosch Configuration Manager” defines also where personal data is stored:
System.Environment.GetFolderPath(System.Environment.SpecialFolder.Personal) – equivalent to the My Documents folder. Usually “C:\Users\<user>\Documents” This member is equivalent to Personal. When option is not selected
System.Environment.GetFolderPath(System.Environment.SpecialFolder.CommonDocuments) equivalent the file system directory that contains documents that are common to all users. Usually “C:\Users\Public\Documents”. When option is selected
In the resolved folder there is a “Bosch\VIDOS” folder created; in current document the path will be named %CM_DOCUMENTS% to ensure unambiguity.
3.2. Information stored in %CM_DOCUMENTS%
CBSLicensing – Device licenses/device fingerprints for licensing
SecurityAndSafetyThings – Azena applications, Azena Device Database
WebView2Cache – Cache folder for WebView 2 controls
CA – Micro CA working folder
Log – logging folder, device communication logs, application logs
Snapshots – Folder JPEG snapshots of camera (currently not in use)
Recordings – Folder for IVA recordings storage
Export – Exchange folder for File Based configuration (users in case of export import of system image)
ConfigurationRepository – Folder for storing device settings backups, configuration snapshots
tmp/Certificates – temporary folder for certificate operations, extracting, archiving
tmp/Syslog – temporary folder for Camera System Logs operations, downloading, archiving
tmp/cm_Update – temporary folder for Configuration Manager updates
tmp/cm_MaintenanceLog - temp folder for Camera Maintenance Log operations, e.g., downloading
tmp/cm_settings – folder for string System Image
Custom views – configuration of custom views in tale view mode
Telemetry – temporary telemetry data – data CM is exposing to analytics endpoint after user agree to share them
4. Security considerations
4.1. Attempting to modify system files or registry entries
CM is not modifying system files beside own configuration files and resources needed for operation. That includes:
HKEY_CURRENT_USER\Software\Bosch\ConfigManager
HKEY_CURRENT_USER\Software\Bosch\VCA
HKEY_CURRENT_USER \Software\Bosch\VIDOS
HKEY_CURRENT_USER \SOFTWARE\Bosch\VideoSDK5
HKEY_CURRENT_USER \Software\Bosch\VideoSDK
HKEY_CURRENT_USER\Software\Bosch\VCA
HKEY_LOCAL_MACHINE\Software\Bosch\ConfigManager
HKEY_LOCAL_MACHINE\Software\Bosch\VIDOS
HKEY_LOCAL_MACHINE\SOFTWARE\Bosch\VideoSDK5
HKEY_LOCAL_MACHINE\Software\Bosch\VideoSDK
HKEY_LOCAL_MACHINE\Software\Bosch\VRM
CM is using mostly its own limited scope in registry to ensure correct operation. Additionally, CM modify following registry settings to ensure interoperation with Web Browser and integration with other Bosch products like Camera Frontend, BT User Hub, Video SDK, integration with web browsers
HKEY_CURRENT_USER SOFTWARE\Classes\btcm
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D12FF18F-AFC2-4E6E-9FEB-8FC4B57FFC93}
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PerfOS\Performance
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\\Services\PerfProc\Performance
HKEY_LOCAL_MACHINE\ Software\Microsoft\Windows\Shell\Associations\UrlAssociations\http\UserChoice
HKEY_LOCAL_MACHINE\Software\Wow6432Node\Bosch\DivarXF\
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\App Paths\Bosch Divar 700 Series*
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall{1E6F8C25-CFF5-4CEC-BE96-89011AB60C89}
HKEY_LOCAL_MACHINE\Software\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall{1E6F8C25-CFF5-4CEC-BE96-89011AB60C89}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall{C439237F-B211-4A96-9FF8-757B40DF534C}
4.2. Trying to communicate with known malicious/external servers
CM communicates only with limited endpoints in internet as presented below
4.3. Demonstrating exploit-like actions (e.g., buffer overflows).
CM is using advanced techniques to manage application memory, there are no intended exploit-like behaviors know, however due to unknown bugs such behavior could be observed, in case of occurrence customers are kindly asked to raise a support ticket.
4.4. Encrypting files (a potential sign of ransomware).
To ensure proper data security lever CM is using strongly encryption using both symmetric and asymmetric algorithms, for data storage, network communication.
5. Network communication
As the Configuration Manager is intended to communicate with devices from different vendors and communication parameters are like host names, ports, protocols, and TLS versions are user configurable it is not possible to provide a finite list of protocols and ports used.
For Bosch devices current network communication settings and security evaluation is available on Configuration Page Network - > Network Services as shown below:
.png?inst-v=351b8a5d-2311-4dca-936f-5d1e8b7ab61e)
